
Legally required security
It is now "consolidated doctrine" (using typical legal terminology) that the scope of security management extends far beyond the technical level. The triad of people, processes and technology is nowadays indisputable in any of the processes that are addressed in the security or continuity of any business or organisation.
However, in one of those convergences that appear as a matter of fact, security managers, CISOs, have found it necessary to move from that consolidated triangle: people, processes and technology, to a perfect square: people, processes, technology and... compliance!
Digital security measures in an organisation
Nowadays, a large part of the security measures that an organisation must implement are requirements backed by some kind of legal standard. Compliance with them is, therefore, inexcusable.
Many will remember the historic Organic Law 15/1999, of 13 December, on the Protection of Personal Data (LOPD) and Royal Ordinance 1720/2007, of 21 December, which approved its implementing regulations. In the legal context that they delimited, and for the data files within their scope of application, a very concrete and specific set of security measures to be implemented and audited were indicated.
For years, these rules regarding the processing of personal data constituted the totality of applicable regulations in the field of information security, but in recent years, they have been silently extending to the current broad panorama, which, it seems, will continue to grow.
Let us review some of the main legal regulations that oblige organisations to implement certain security measures:
- The National Security Framework, approved in 2010, subsequently updated through RO 951/2015, and recently through RO 311/2022: This standard aims to "create confidence in the use of electronic media, through measures to ensure the security of systems, data, communications and electronic services". Although its scope of application initially appears to be limited to public administrations, since its first version, it has also been tacitly applied to private organisations that provide services to these public administrations.
- The EU 2016/679 of the European Parliament and of the Council, of 27 April, which regulates the protection of natural persons with regard to the processing of personal data. Known as the GDPR, it defines obligations aimed, among other principles, at ensuring the security of such data. This regulation, which is directly applicable, was accompanied by the new Organic Law 3/2018, of 5 December, on the Protection of Personal Data and Guarantee of Digital Rights, which also defines criteria for the adoption of security measures.
- Law 8/2011, of 28 April, establishing measures for the protection of critical infrastructures, which, although substantially oriented towards the protection of facilities, aims to "regulate the protection of critical infrastructures against deliberate attacks of all kinds (both physical and cybernetic)".
- Royal Ordinance 12/2018, of 7 September, on the security of networks and information systems, which transposed the so-called NIS Directive into Spanish law. The national regulation identifies those essential sectors in which it is necessary to guarantee the protection of networks and information systems.
- Royal Ordinance 43/2021, of 26 January, which develops the previous one "as regards the strategic and institutional framework for the security of networks and information systems, the supervision of compliance with the security obligations of operators of essential services and digital service providers".
The list could be extended much further by including other regulations of a more limited or sectoral scope: the national security strategy, the e-IDAS regulation, Law 59/2003 of 19 December on electronic signatures or Law 5/2014 of 4 April on Private Security, which already includes in its scope of application companies providing IT security services whose requirements may be developed in a specific royal ordinance.
Each organisation can (must) analyse and manage its risks, i.e. mitigate, reduce or transfer them
How to implement a digital security strategy
It should be noted at this point that the publication of these new legal regulations introduced, to a greater or lesser degree, a substantial and extraordinarily important change of approach with respect to the LOPD. The texts no longer included a concrete, specific and discrete set of required security measures. On the contrary, risk analysis has been substantiated as the way to determine the taxonomy and scope of the necessary security measures. In short, each organisation can (must) analyse and manage its risks, i.e. mitigate, reduce or transfer them.
Legislation generates obligations, establishes supervisory and sanctioning mechanisms, especially in critical and essential sectors, and the undisputed trend is the progressive enlargement of the set of obliged legal subjects (see the recent revision of the NIS 2 Directive, which already refers to important sectors).
In this scenario, as we indicated at the beginning of this post, information security management in organisations must integrate the traditional pillars of people, processes and technology with the new, and not minor, pillar of compliance.
And we must speak of integration, not incorporation. The traditional pillars, the management model, the processes associated with the analysis and treatment of risks and, in short, the strategy, must be aligned in a defined and implemented safety management system, and it is in this same management system where we must integrate compliance management, which, like the others, is not a situation, but a process.
This comprehensive vision of the security strategy forms part of the core of Izertis' value offer. From this approach, our methodology addresses the diagnosis (where we are), the objective risk scenario (where we should be) and the action plan (how to achieve it) taking consider these four areas of action: people, processes, technology and compliance.
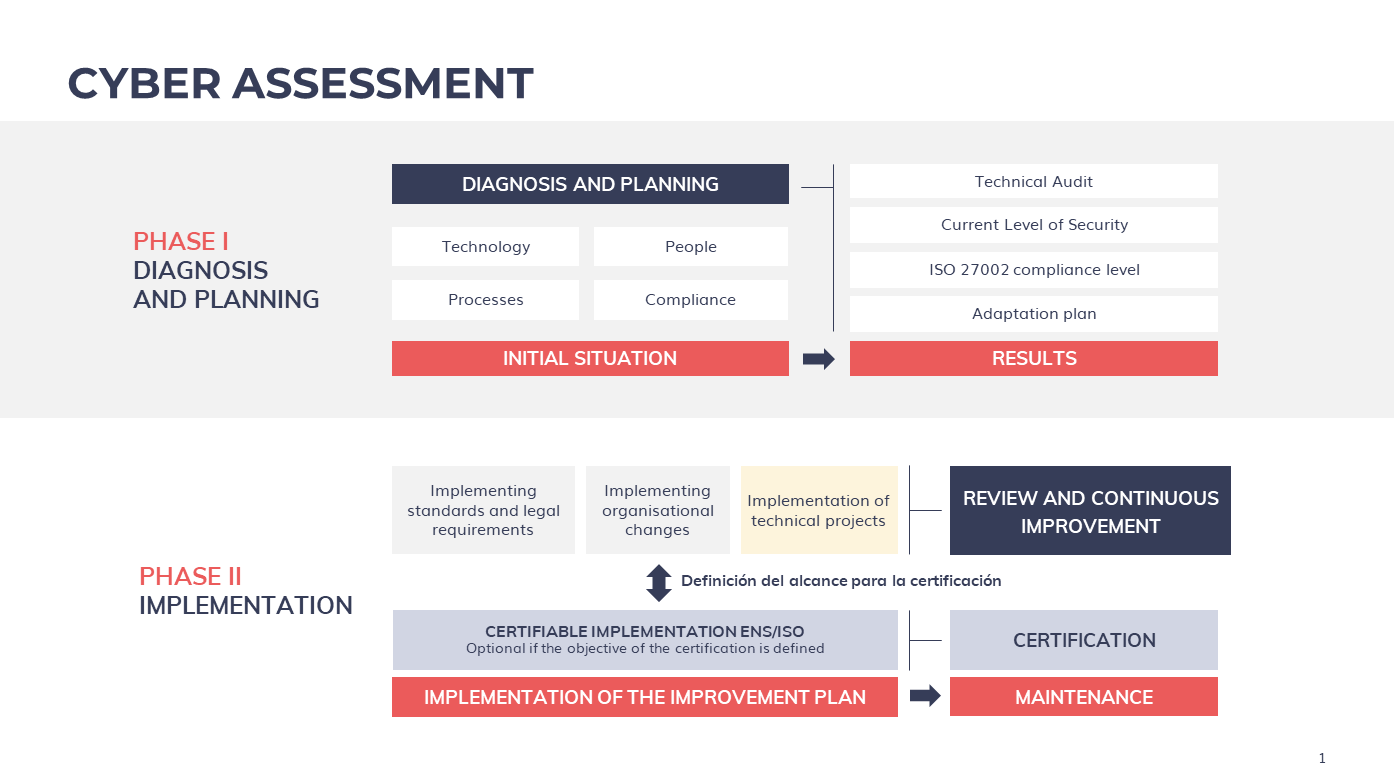
Maintaining compliance is a new challenge for organisations, inexcusable due to its regulatory status, and must be integrated into the strategic security management model, especially when the objectives of this strategy include the implementation of an Information Security Management System.
Doing it so also reflects an efficient and transparent attitude of the organisation towards customers, suppliers, investors, authorities and other stakeholders; it builds trust and reputation and undoubtedly contributes to business development by improving the organisation's competitiveness.

